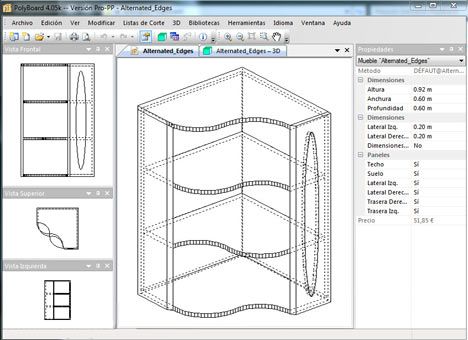
PolyBoard displays the three cabinet 2D views (front, top, and side), and a 3D rendering in relation to material colors and textures. The PolyBoard built-in 3D function offers several predefined views, and various zoom and rotation tools, which help setting the wished 3D view. PolyBoard also offers a DXF 3D_Face export function, compatible with most CAD software, such as AutoCad, VectorWorks, KitchenDraw, etc … PolyBoard cabinets cutting lists are recalculated in real time, taking into account specified materials, possible oversizings, and plated edges thickness. Cutting lists are exported in OptiCut format, as well as in a «Text» format compatible with most spreadsheets and cutting optimization software.
CLICK HERE TO DOWNLOAD